Extracting firmware images from SPI flash
Recently I’ve been revisiting some hardware hacking techniques. I purchased a Hydrabus and a standard SOIC-8 clip from DigiKey to assist with this task. For practice, I decided I wanted to attempt to extract the firmware from the same DVR system I experimented with back in 2015. Link to post.
After inspecting the circuit board, I found a flash memory chip on the back.
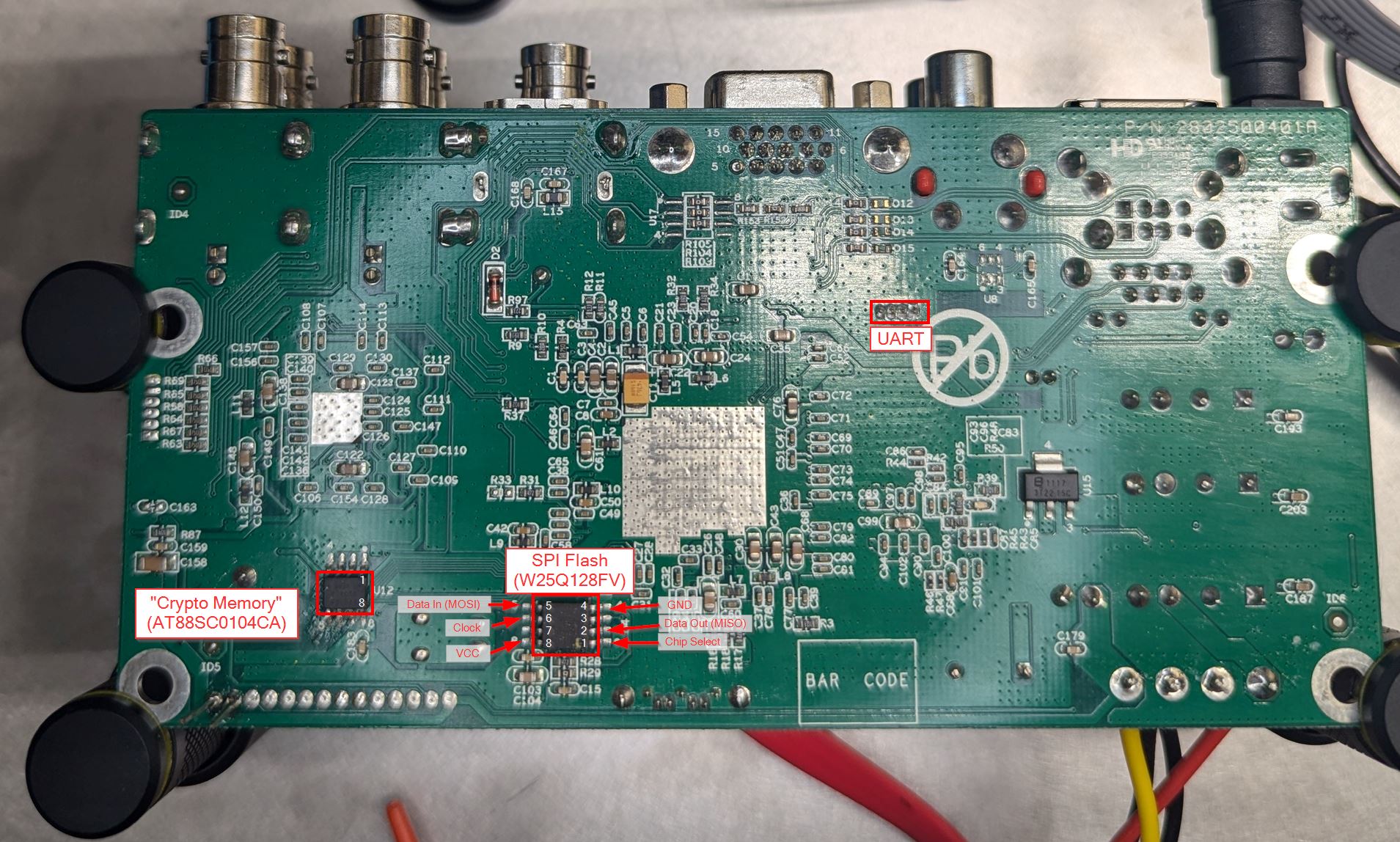
Some careful lighting adjustments revealed the chip was a Winbond W25Q128FV, which is supported by flashrom.
I then connected the SOIC clip to the chip and then matched the pinout from the datasheet.
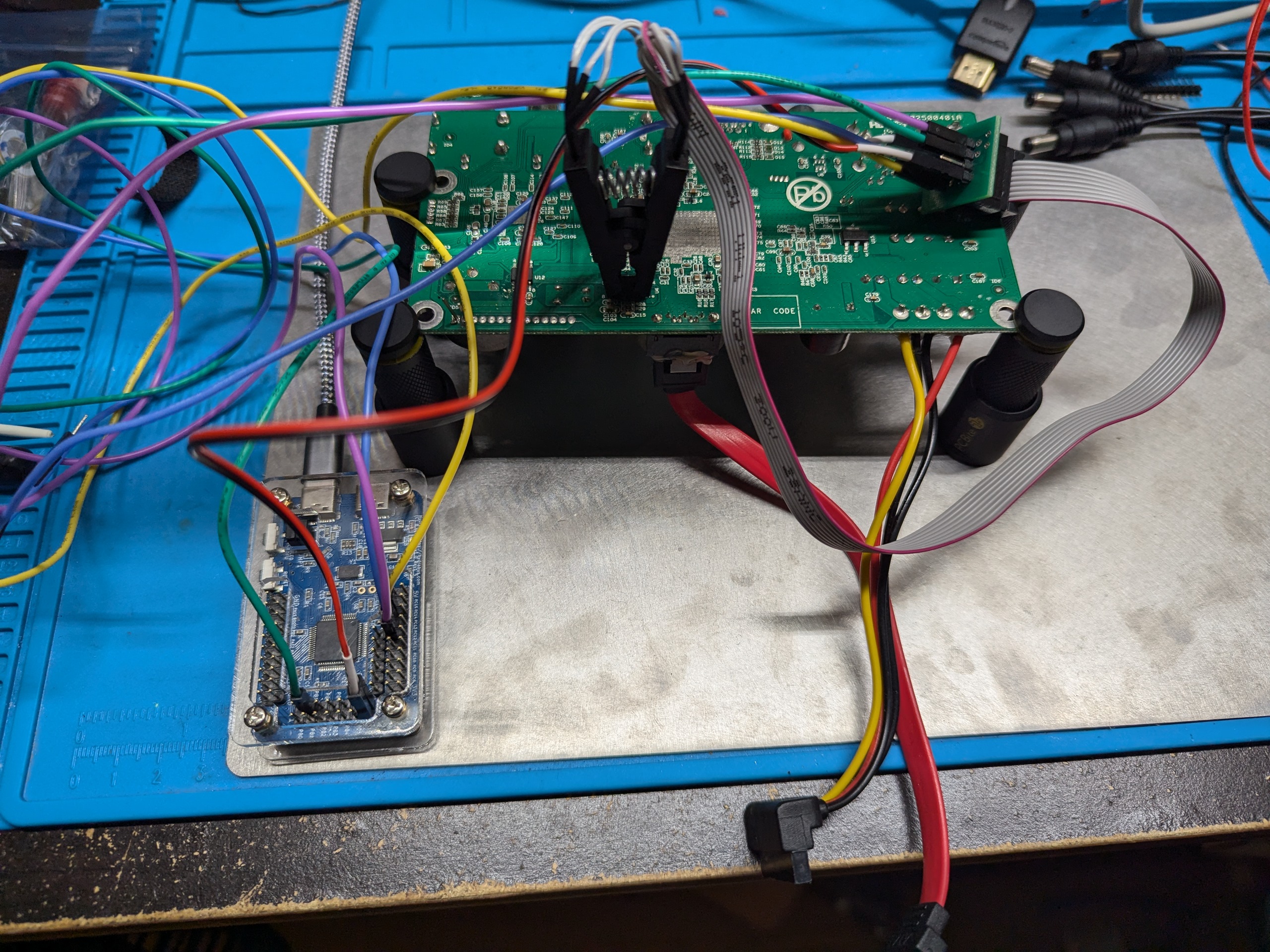
| Chip Pin | Function | Hydrabus Pin | Hydrabus function |
|---|---|---|---|
| 1 | Chip Select (CS) | PC1 | SPI 2 Chip Select |
| 2 | Data Out (DO) | PC2 | SPI 2 MISO |
| 2 | Write Protect (WP) | - | - |
| 4 | Ground (GND) | GND | Ground |
| 5 | Data In (DI) | PC3 | SPI 2 MOSI |
| 6 | Clock (CLK) | PB10 | SPI2 CLK |
| 7 | Hold/Reset | - | - |
| 8 | Voltage Supply (VCC) | 3v3 | 3.3 Volt Supply |
Extracting the memory is as simple as
flashrom -p /dev/ttyACM0 -r dvr_rom.bin
Unfortunately, the /etc/passwd file was not found on the device. This may mean that the password is set at runtime. Further investigation is needed. There is also a second chip on the board which is an Amtel AT88SC0104CA. This chip is listed as a 1kb to 8kb “CryptoMemory”. I’ve tried sniffing the I2C messages, but have not seen anything that looks like a password. That will be discussed in a another post.